 https://youtu.be/06jmo8IIFtg
https://youtu.be/06jmo8IIFtgCreated: 07/01/2025 22:12 Last Updated: 12/01/2025 01:04
SOC team got an alert on their SIEM about the possible exploitation of CVE-2024-21320. The analyst on site captured the triage and relevant network capture as well to assist in this crucial investigation.
 https://youtu.be/06jmo8IIFtg
https://youtu.be/06jmo8IIFtg
CVE-2024-21320 is a vulnerability involving Microsoft Themes that the threat actor can craft a theme file that will fetch resource from the threat actor SMB server then trick a victim to open it which will trigger automatic thumbnail creation by Explorer process which also sending SMB handshake packets to the threat actor machine including NTLM hash of the victim who opened the theme file which then the threat actor can crack it and login to the victim machine later.
Resource: - https://www.rbtsec.com/blog/cve-2024-21320-windows-themes-spoofing-vulnerability-walkthrough/ - https://www.akamai.com/blog/security-research/leaking-ntlm-credentials-through-windows-themes
Now we can start our investigation
Can you identify the Attacker's file share path utilized to exploit the CVE?
Lets check out what we have first, there are 2 folders on the desktop which are ChallengeFile that contains evidence files collected by KAPE and ntlm.pcapng file.
We have bunch of tools as our disposal so lets just start with pcapng file first and come back to this when we really them.
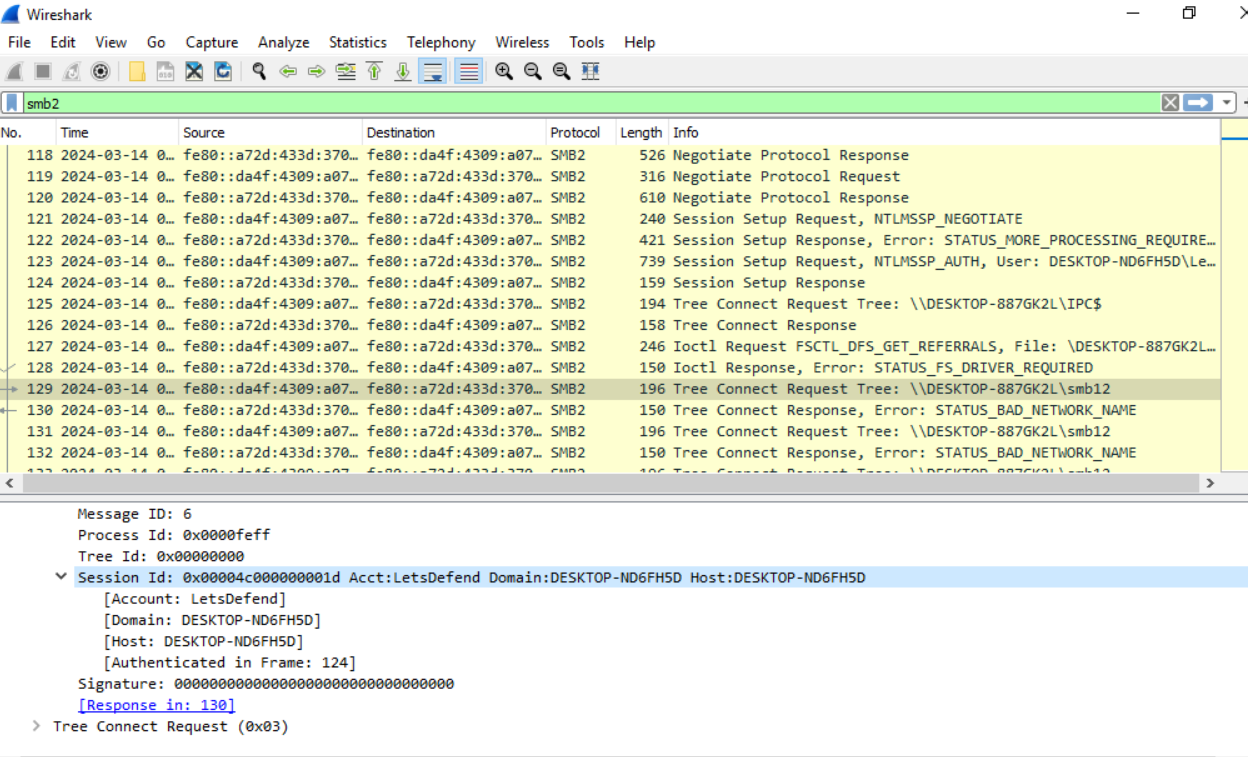
After opened ntlm.pcapng with Wireshark and filtered with smb2 for SMB 2 protocol then we can see that there are several attempts to fetch resource from \\DESKTOP-887GK2L\smb12 and this is the file share path that we are looking for.
\\DESKTOP-887GK2L\smb12
Victim's NTLM hash was relayed to the attacker's server allowing them to capture the hash and either use it in NTLM relay attacks or crack the hash. What is the Full Username of the compromised account?
Answer Format: DOMAIN\Username
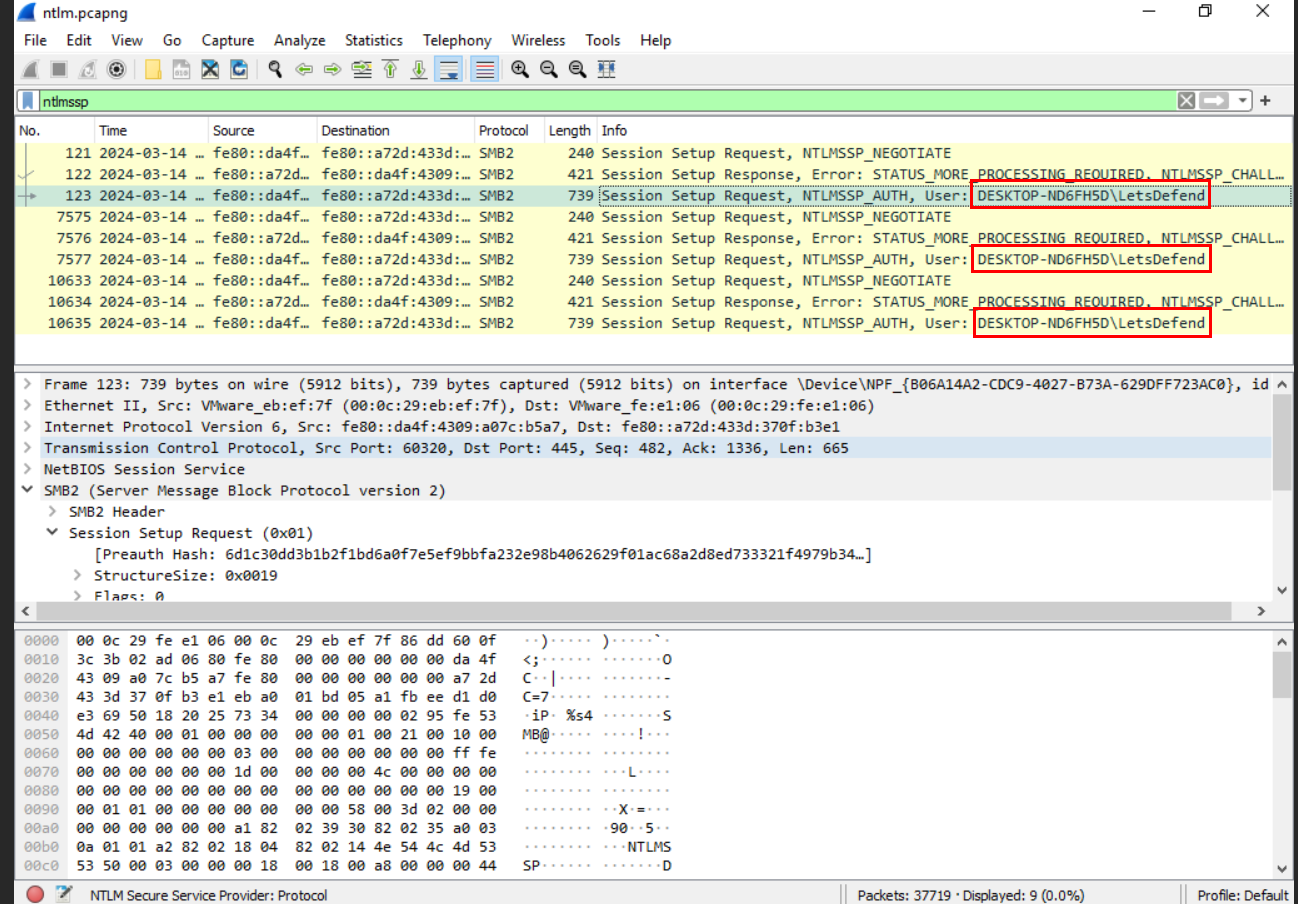
We can filter ntlmssp for NTLMSSP which is a protocol for Authentication using NTLM protocol which we can see that there are 3 Session Setup Requests using NTLMSSP_AUTH by "DESKTOP-ND6FH5D\LetsDefend" user and by sending these request then the attacker will be able to capture NTLM hash of this user.
DESKTOP-ND6FH5D\LetsDefend
The victim's credentials were relayed to attackers 3 times. Considering only the packets related to the first relay, what is the NTLM Server challenge used in the NTLM negotiation?
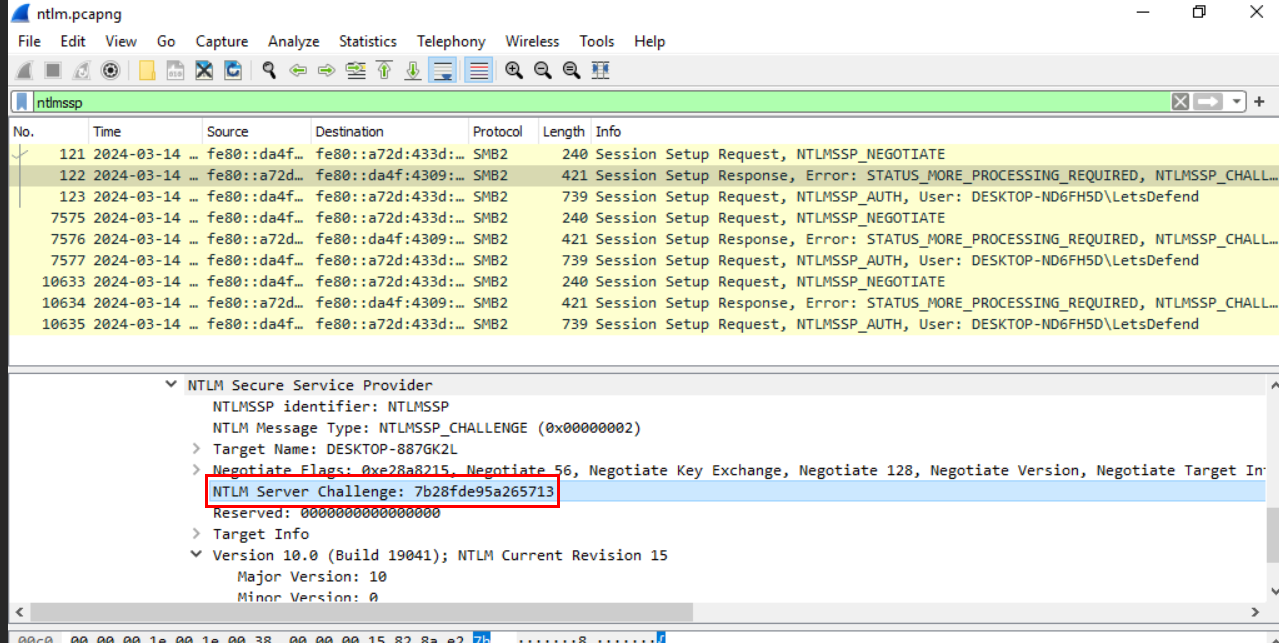
Lets select packet number 122 which is the first Session Setup Response Error packet then by inspecting
SMB2 (Server Block Message Protocol version 2) -> Session Setup Request (0x01) -> Security Blob: ... -> GSS-API ... -> Simple Protected Negotiation -> negTokenTarg -> NTLM Secure Service Provider -> NTLM Server Challenge
Then we will be able to get the NTLM Server Challenge used for this NTLM negotiation right here.
7b28fde95a265713
What is the NTProofStr value in the NTLM negotiation?
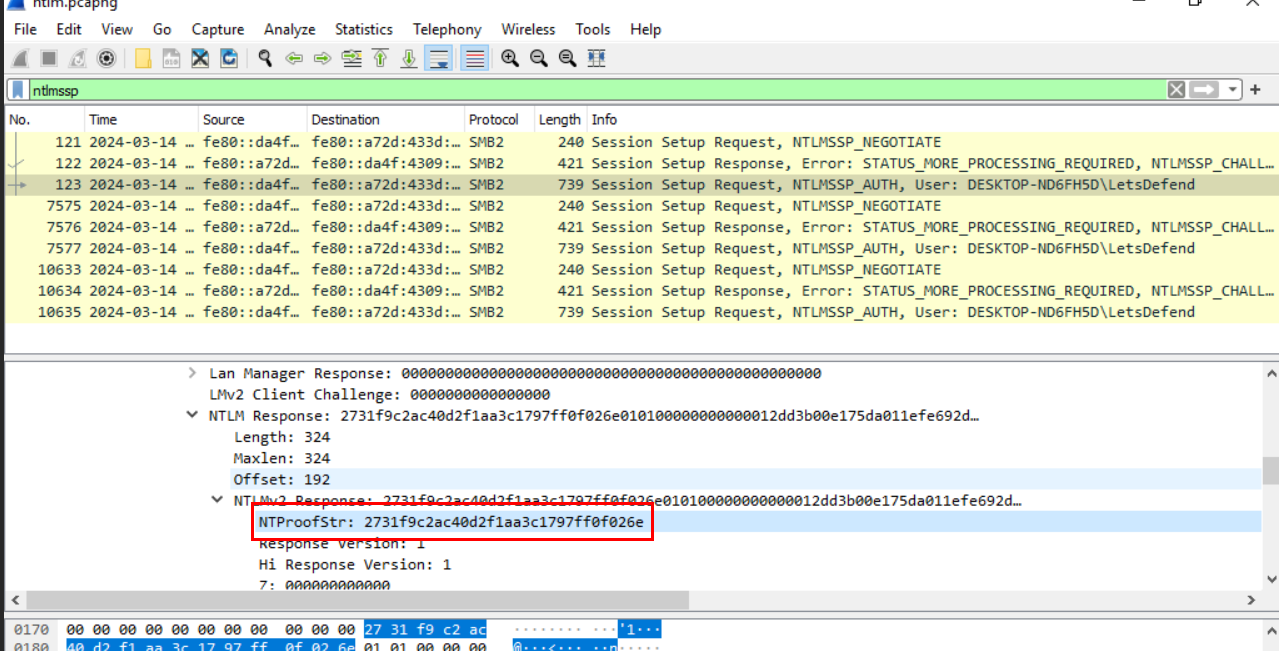
Now lets move to packet number 123 and inspecting
SMB2 (Server Block Message Protocol version 2) -> Session Setup Request (0x01) -> Security Blob: ... -> GSS-API ... -> Simple Protected Negotiation -> negTokenTarg -> NTLM Secure Service Provider -> NTLM Response: ... -> NTLMv2 Response: ... -> NTProofStr
Then we should be able to retrieve NTProofStr value of this NTLM negotiation right here.
2731f9c2ac40d2f1aa3c1797ff0f026e
Security team saw an RDP connection from the Attacker's internal machine to the compromised victim's machine, a day after the CVE was exploited. When did the attacker log on successfully?
Answer Format: (YYYY-MM-DD HH:MM:SS)
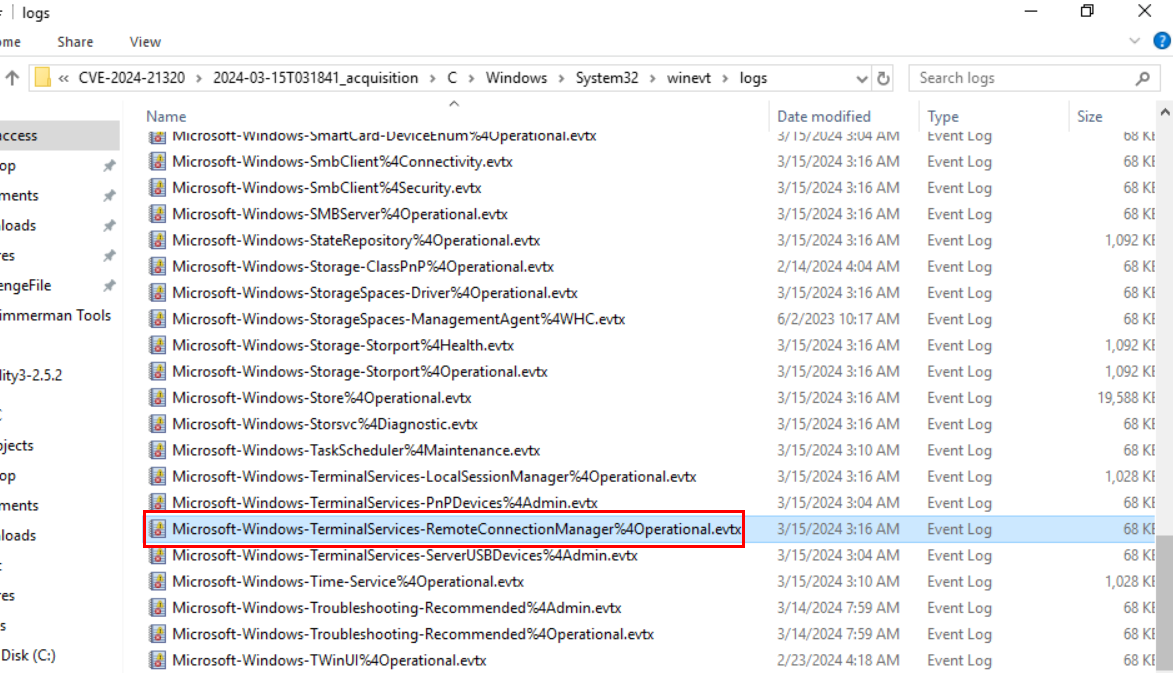
To find out about this, we have to inspect this Windows Event log which focuses on remote connections to a machine, particularly for Remote Desktop Protocol (RDP) sessions.
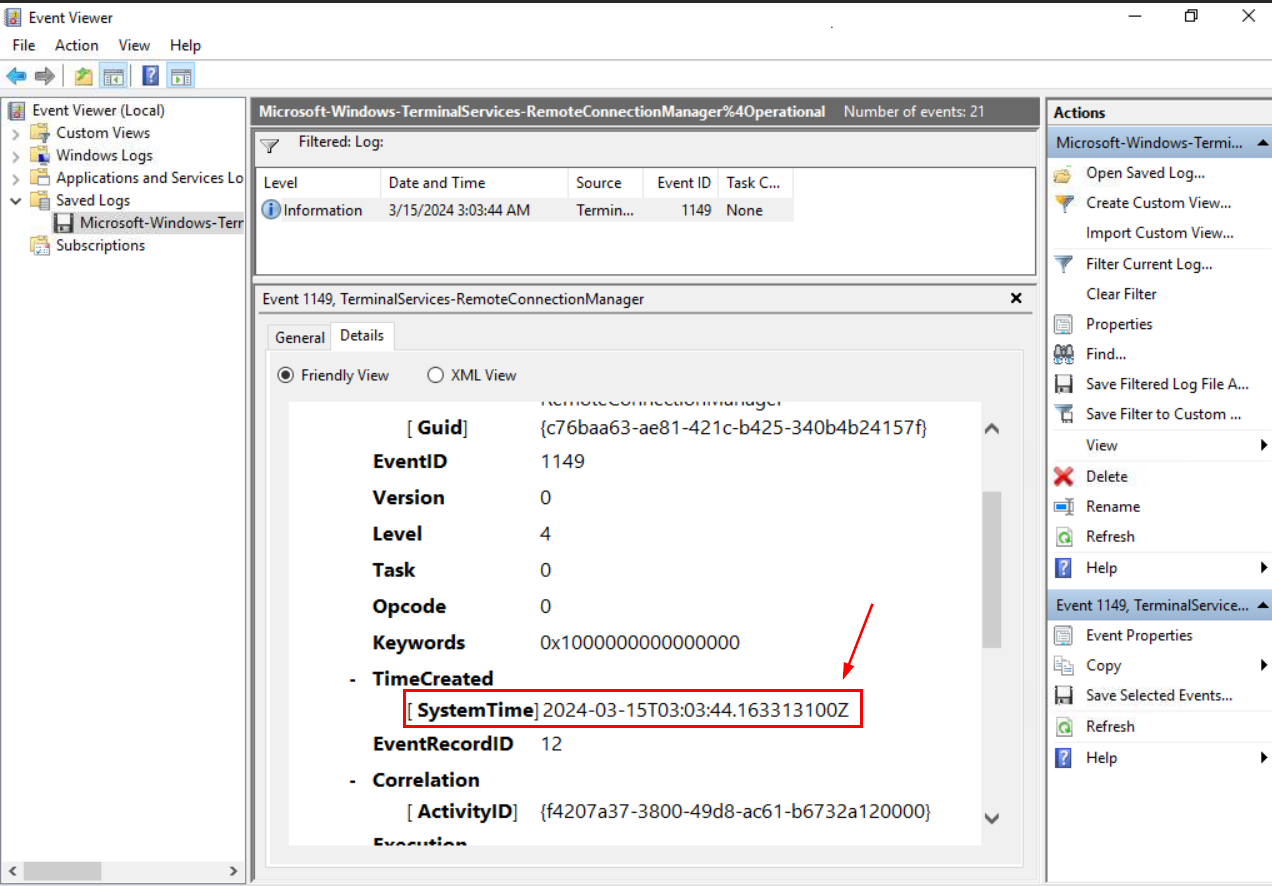
By filtering Event ID 1149 (A successful Remote Desktop connection attempt is made.) on Terminal Services Remote Connection Manager (Operational) log then we should only have this 1 event right here which happened at "2024-03-15 03:03:44"
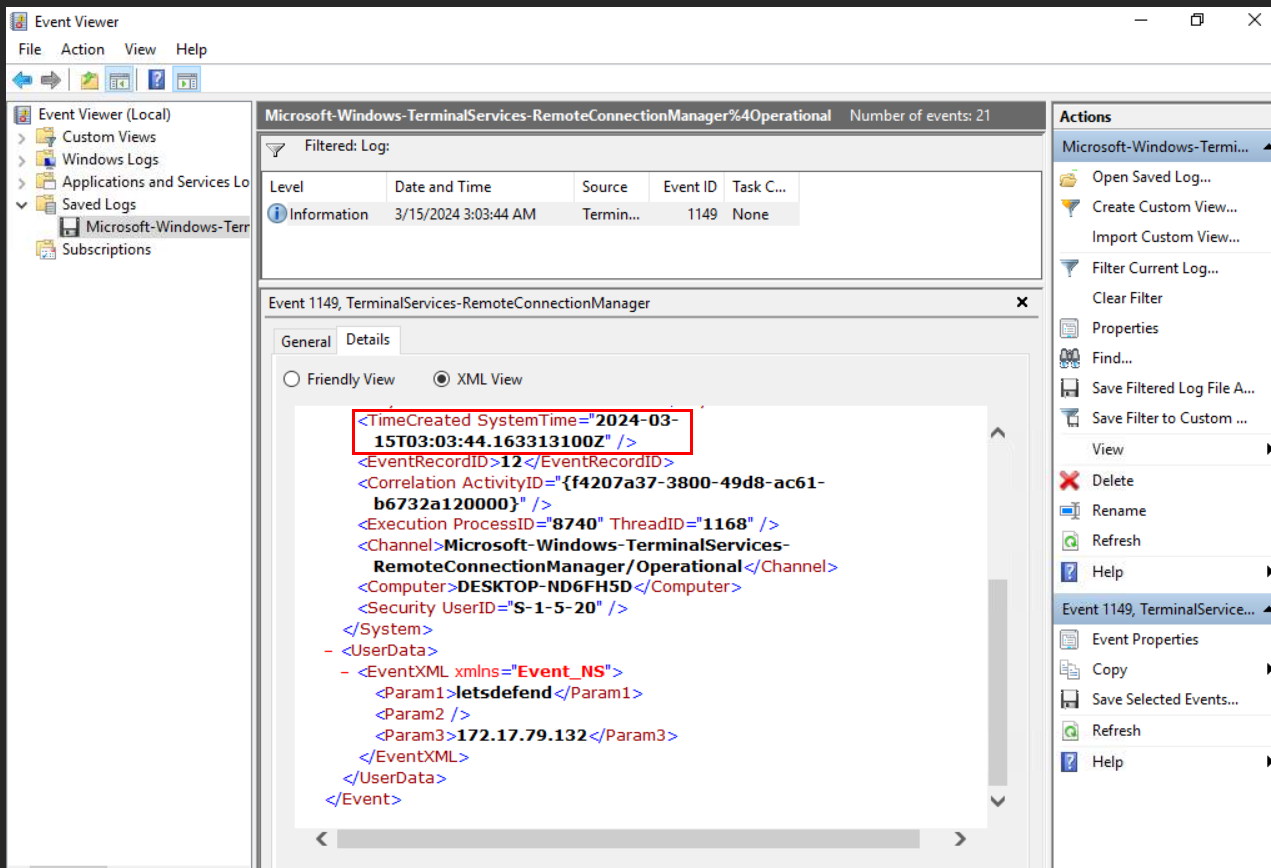
Then we can also see that "172.17.79.132" was the source IP of the attacker which successfully cracked "letsdefend" user password and connected to the victim machine via RDP
2024-03-15 03:03:44
Tracing back to the start of the exploitation, what was the name of the file used to exploit the victim and exploit the cve. Please detail the full path of the file.
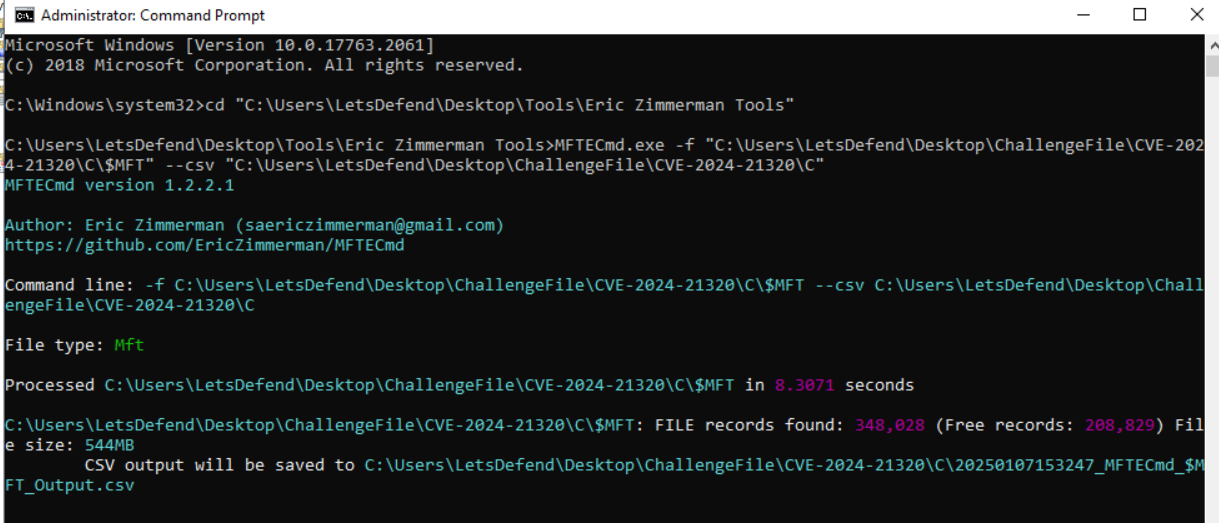
We know that this CVE can be exploited tricking user to open crafted theme file so we can use MFTECmd.exe (EZ tool) on $MFT to parse Master File Table then we will be able to search for the theme file from the output of this tool.
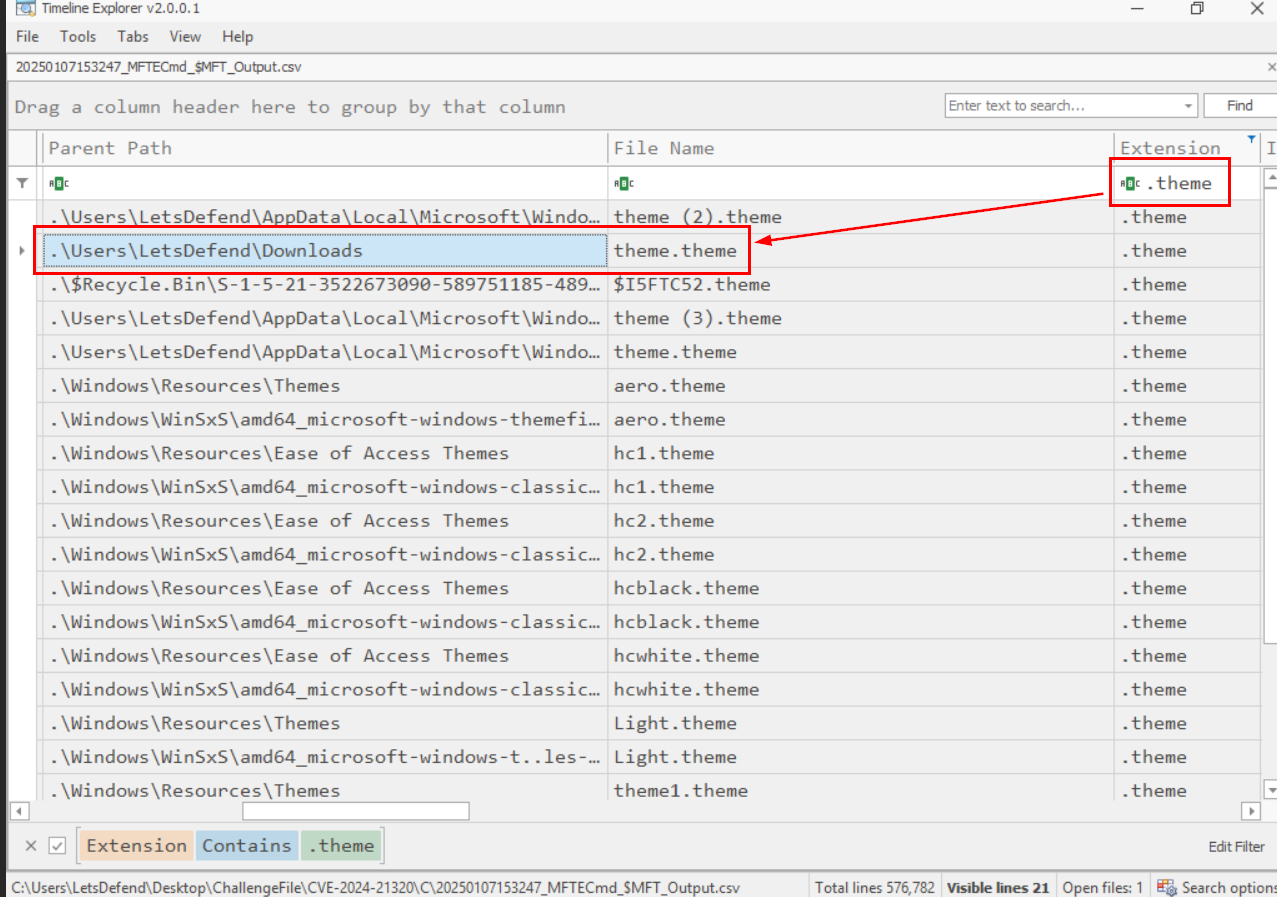
Open the output from MFTECmd.exe with "Timeline Explorer" and just simply search for .theme extension and now we can see that there is a suspicious theme file that we are looking for located at the LetsDefend user's Downloads folder.
C:\Users\LetsDefend\Downloads\theme.theme
Attacker downloaded a Powershell script on the system, to further their objectives. What is the name of the script?
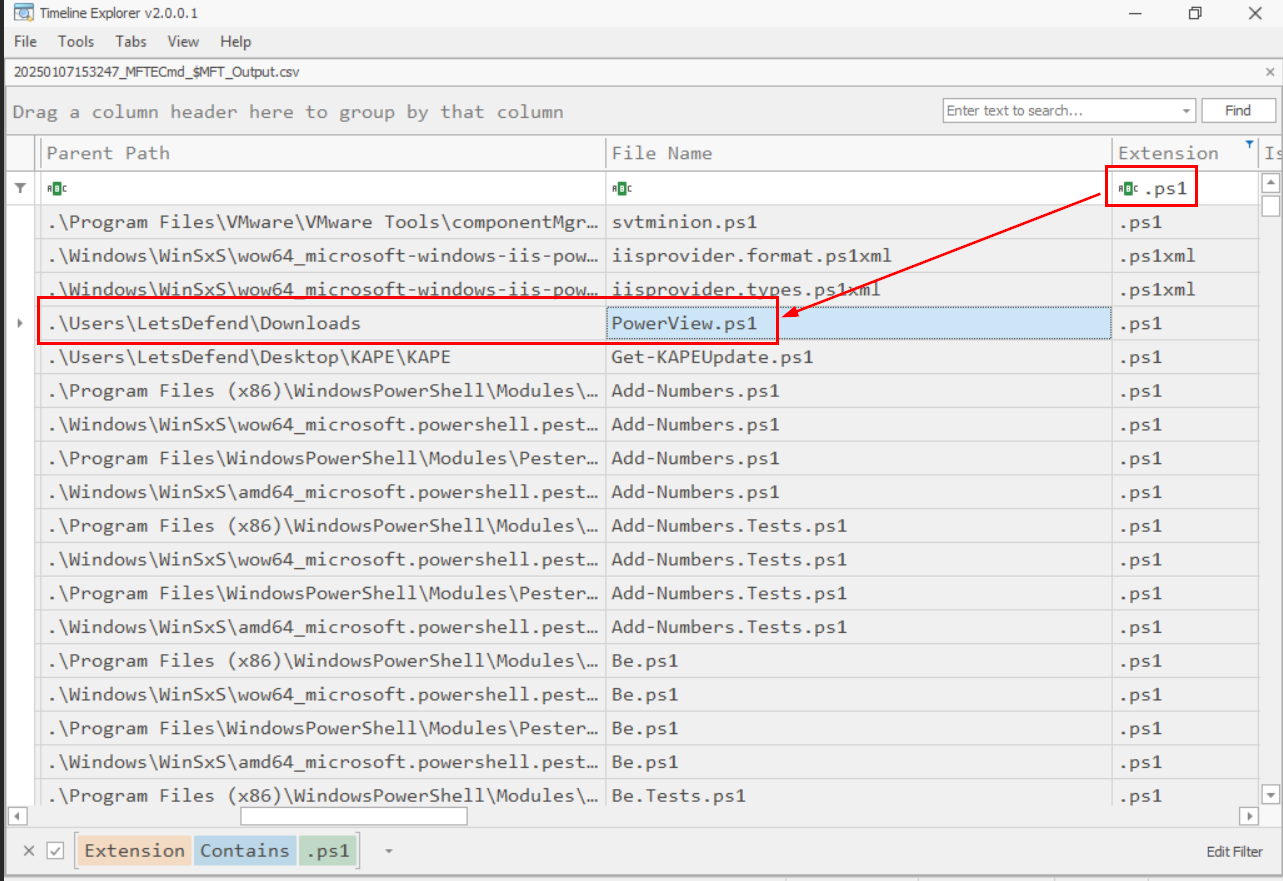
Now we will change our search term to .ps1 extensino then we can see that PowerView.ps1 is the one we are looking for and this script can gather detailed information about an Active Directory environment for reconnaissance and lateral movement.
PowerView.ps1
Attacker Added a backdoor account for persistence mechanisms. What is the username and password of the newly created account?
Answer Format: Username:Password
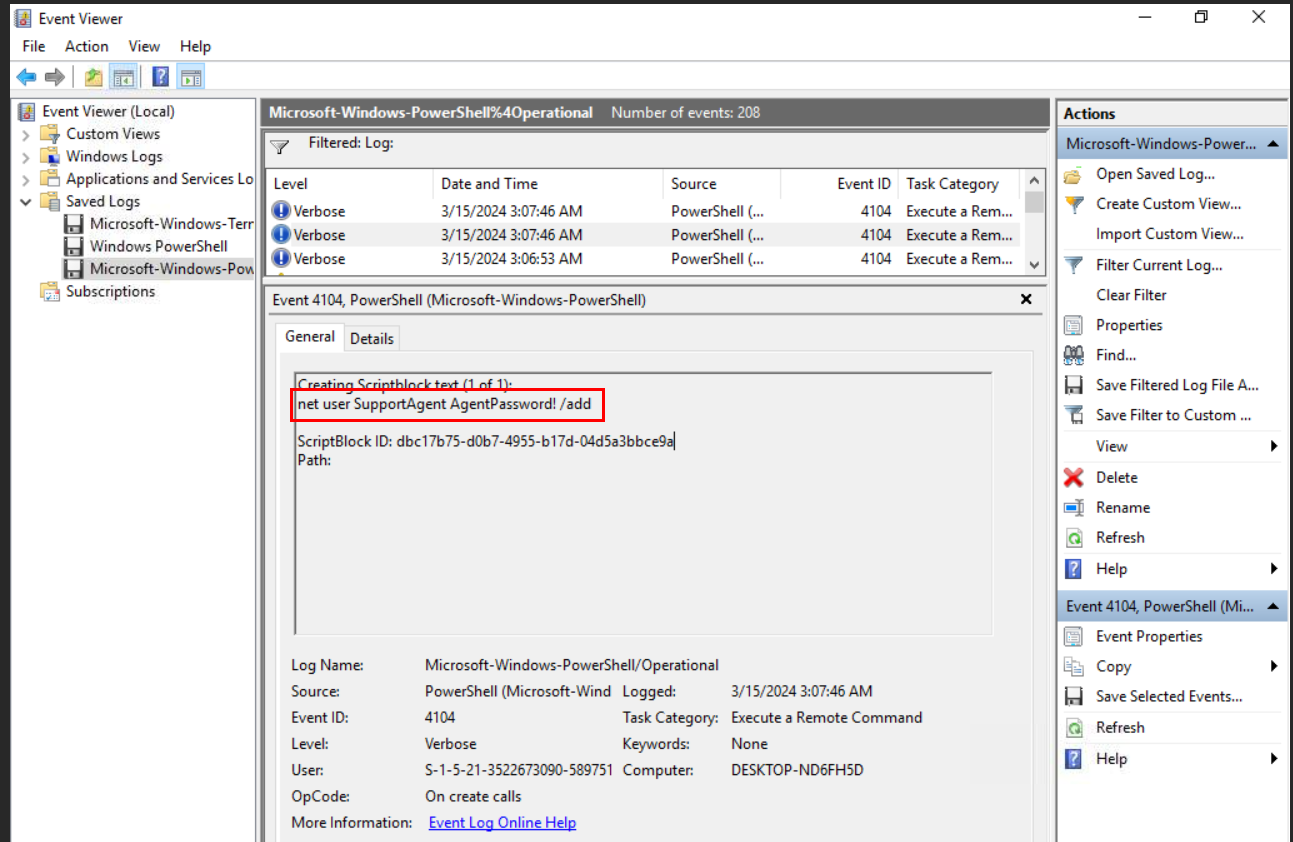
This time, we will have to check PowerShell commands then focus on Event ID 4104 for ScriptBlockLogging and we will see that the new user was created via PowerShell with net user SupportAgent AgentPassword! /all.
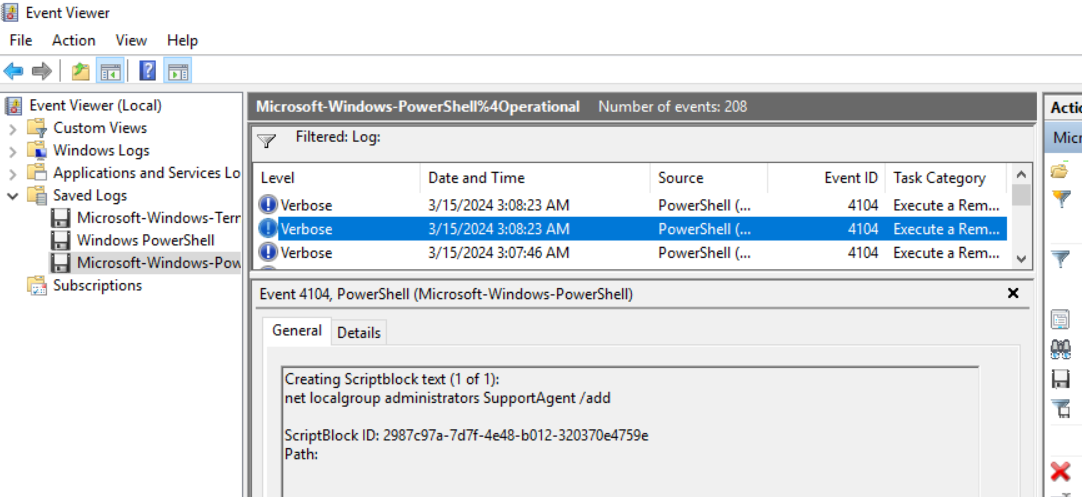
We can also see that this user was also added to "administrators" group after successfully created.
SupportAgent:AgentPassword!
On this challenge, we got to know how CVE-2024-21320 works along with the way to detect it (such as capturing network traffic) then we also used Windows event log and Master File Table record to find out what happened after the attacker successfully exploited this vulnerability.